Nov 04 2021
Securing Data with the Laws of Physics
 Data security sounds like a boring topic. However, it is quickly becoming one of the most important technologies in our modern world. Our data, communications, and transactions are increasingly digital, and they are all vulnerable to hacking. It’s estimated that hacking costs the world about $6 trillion per year as of 2021, and increasing. Slightly more than half of data breaches are due to hacking (the rest to some form of social engineering, like phishing). Cyberwarfare is now the new warfare between developed nations, and critical infrastructure may be vulnerable to hacks. Companies are now under constant attack by ransomware. Individuals may have their digital identities stolen, losing their savings and disrupting their lives.
Data security sounds like a boring topic. However, it is quickly becoming one of the most important technologies in our modern world. Our data, communications, and transactions are increasingly digital, and they are all vulnerable to hacking. It’s estimated that hacking costs the world about $6 trillion per year as of 2021, and increasing. Slightly more than half of data breaches are due to hacking (the rest to some form of social engineering, like phishing). Cyberwarfare is now the new warfare between developed nations, and critical infrastructure may be vulnerable to hacks. Companies are now under constant attack by ransomware. Individuals may have their digital identities stolen, losing their savings and disrupting their lives.
About half of the problem is individual behavior, and this can be mitigated through education, company and governmental policies, and improved tools. But the other half is not due to any failure of personal behavior, but rather to straight-up hacking. This problem requires new technology to fix (in addition to institution-level responsibility to secure systems as much as possible). One aspect of hacking-resistance is authentication – you need a code to get into a system. This is the focus of a potential incremental advance in authentication systems, but let’s give some further background first.
Authentication involves a prover and a verifier. They might, for example, share a code, and the prover needs to provide the code to the verifier to confirm their identity. The inherent problem with this system is that the prover, by necessity, has to give up personal information (such as their code) during the verification process, and this is a point of attack for a hacker. To solve this problem, in the 1980s, programmers developed so-called “zero-knowledge proofs”. The idea is that the prover can demonstrate they have the code without giving up the code itself, and so it remains secure.
The primary way to construct a system for zero-knowledge proofs is to use a very complicated mathematical puzzle or calculation. The prover can then provide part or all of the solution, without revealing anything about the method of arriving at the solution. It’s like giving the answer without the hacker knowing the question, and since the answer changes each time, the hacker has no way of knowing what the next correct answer is supposed to be. He needs to hack the question.
The problem with this method is that it is based on the complex puzzle. However, these systems are based on the assumption that a specific encoding system is difficult to decode. Increasing hardware and software technology is making it easier for hackers to decode these systems, rendering them impotent. The first country to achieve “quantum superiority” with a workable quantum computer will have the ultimate cybersecurity advantage, with a system that can potentially hack any security in the world.
Now we get to the news item – a potential zero-knowledge proof not based on an encoded system but based on the laws of physics, specifically relativity. The idea is that two systems with the same code will verify be able to prove the code (without giving away all the information – so zero-knowledge) faster than the two systems can communicate in order to cheat (presumably by a hacker). This is based on the relativistic concept that information can never ever travel faster than the speed of light. So far this principle has born out, and it is very likely that this is a fundamental law of the universe that can never be broken.
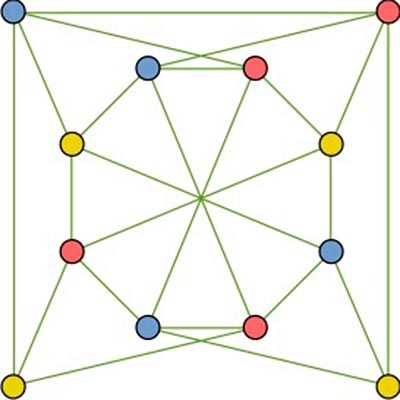
If you have two systems that are far enough away (and this does not have to be that far, just 60 meters), they can calculate faster than they can communicate even in theory. The zero-knowledge proof system used in these experiments is the three color problem. Let’s say you have dots that can be one of three colors, and these dots (nodes) are connected in some network pattern. The problem is to make sure that no two nodes of the same color are connected. The prover can demonstrate to the verifier that it has a solution to a particular three-color puzzle by indicating the color of specific nodes. One puzzle can contain millions of nodes and connections, creating a problem impossible to solve by conventional computers (although potentially solvable by a powerful enough quantum computer, but that is not an issue for now). This is a zero-knowledge solution because the prover does not have to provide the entire puzzle solution. They can just demonstrate knowledge of a subset of pairs, enough to make it essentially impossible to guess but not enough to give away the entire code. Because the systems are far enough away, there is no way for a hacker to get the information from the verifier in time.
This sounds pretty secure, and may be the next thing in cybersecurity. Of course the “unhackable” system is akin to the “unsinkable” ship. Such claims often prove ironic. Rather, we need to look at cybersecurity as an arms race. We need to keep one step ahead of the hackers, but at no point do we have a forever unhackable system.
Hopefully this process will work and give another layer of security for a while. But the bigger picture is that we need to invest a great deal more money and resources into cybersecurity. The breaches of major companies and utilities over the last year prove this is a serious problem, and we ignore it at our own peril.






